QUESTION 71
Refer to the exhibit. Which statement about this output is true? 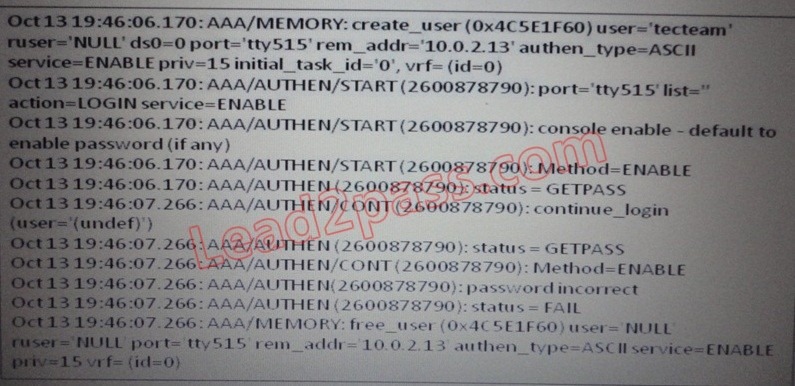
A. The user logged into the router with the incorrect username and password.
B. The login failed because there was no default enable password.
C. The login failed because the password entered was incorrect.
D. The user logged in and was given privilege level 15.
Answer: C
QUESTION 72
Refer to the exhibit. Which traffic is permitted by this ACL? 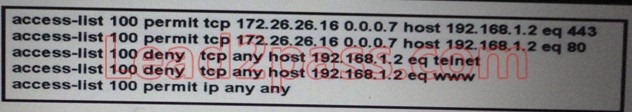
A. TCP traffic sourced from any host in the 172.26.26.8/29 subnet on any port to host 192.168.1.2 port 80 or 443
B. TCP traffic sourced from host 172.26.26.21 on port 80 or 443 to host 192.168.1.2 on any port
C. any TCP traffic sourced from host 172.26.26.30 destined to host 192.168.1.1
D. any TCP traffic sourced from host 172.26.26.20 to host 192.168.1.2
Answer: C
QUESTION 73
Refer to the exhibit. Which statement about this partial CLI configuration of an access control list is true? 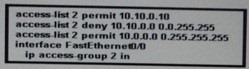
A. The access list accepts all traffic on the 10.0.0.0 subnets.
B. All traffic from the 10.10.0.0 subnets is denied.
C. Only traffic from 10.10.0.10 is allowed.
D. This configuration is invalid. It should be configured as an extended ACL to permit the associated wildcard mask.
E. From the 10.10.0.0 subnet, only traffic sourced from 10.10.0.10 is allowed; traffic sourced from the other 10.0.0.0 subnets also is allowed.
F. The access list permits traffic destined to the 10.10.0.10 host on FastEthernet0/0 from any source.
Answer: E
QUESTION 74
Which type of Cisco ASA access list entry can be configured to match multiple entries in a single statement?
A. nested object-class
B. class-map
C. extended wildcard matching
D. object groups
Answer: D
QUESTION 75
Which statement about an access control list that is applied to a router interface is true?
A. It only filters traffic that passes through the router.
B. It filters pass-through and router-generated traffic.
C. An empty ACL blocks all traffic.
D. It filters traffic in the inbound and outbound directions.
Answer: A
QUESTION 76
You have been tasked by your manager to implement syslog in your network. Which option is an important factor to consider in your implementation?
A. Use SSH to access your syslog information.
B. Enable the highest level of syslog function available to ensure that all possible event messages are logged.
C. Log all messages to the system buffer so that they can be displayed when accessing the router.
D. Synchronize clocks on the network with a protocol such as Network Time Protocol.
Answer: D
QUESTION 77
Which protocol secures router management session traffic?
A. SSTP
B. POP
C. Telnet
D. SSH
Answer: D
QUESTION 78
Which two considerations about secure network management are important? (Choose two.)
A. log tampering
B. encryption algorithm strength
C. accurate time stamping
D. off-site storage
E. Use RADIUS for router commands authorization.
F. Do not use a loopback interface for device management access.
Answer: AC
QUESTION 79
Which command enables Cisco IOS image resilience?
A. secure boot-<IOS image filename>
B. secure boot-running-config
C. secure boot-start
D. secure boot-image
Answer: D
QUESTION 80
Which router management feature provides for the ability to configure multiple administrative views?
A. role-based CLI
B. virtual routing and forwarding
C. secure config privilege {level}
D. parser view view name
Answer: A
New Updated Passleader Cisco 640-554 Exam Dumps Free Download